There has been a dramatic increase in phishing attacks directed at the UF community since the start of this calendar year (2017).
Email messages, websites, and phone calls that are designed to steal money either by tricking you into installing malicious software or revealing personal information about yourself or stealing it from your computer are commonly called phishing. It is estimated that 91% of all cyberattacks begin with some sort of social engineering attack like this and can lead to substantial financial losses. Last year alone phishing contributed to approximately $3 billion in fraudulent tax return filings.
Since January 1st, 2017 phishing attacks directed against UF have become substantially more sophisticated. Already there have been more than 100 Gatorlink accounts compromised through at least 13 unique, UF branded phishing attacks. These UF-branded attacks have used complete, and accurate, clones of the UF Login page and have copied/pasted language directly from UF’s IT Alerts page into their own emails. The malicious actors are also increasingly aware of UF procedures and are attempting to edit individuals W2 and payroll direct deposit information.
As you can see, these attacks are becoming more common and harder to recognize. They not only lead to security compromises to UF information but can directly, and immediately, impact your pocketbook.
UF is constantly reviewing and improving recognition of these attacks. Additional safeguards in UF processes are in the works now. The best defense, however, is an educated and aware user community so here are a few tips for recognizing a phish attack on your own:
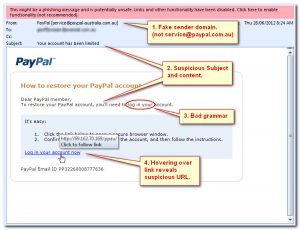
- Look for bad spelling and grammar. Cybercriminals are not known for their grammar and spelling since they don’t have the staff of copy editors that larger organizations and companies would have for their mass mailing campaigns. If you notice mistakes in an email, it may be a scam.
- Pay attention to links in email. If you see a link in a suspicious email message, first, and foremost, don’t click on it. Rest your mouse (but don’t click) on the link to see if the address matches the link that was typed in the message. In the example below the link reveals the real web address, as shown in the box with the yellow background. The string of cryptic numbers looks nothing like the company’s real web address.
- Disregard emails with threats (out of quota, expiration of account, etc). Have you ever received a threat that your account would be closed if you didn’t respond to an email message or if you didn’t verify your account at a webpage? Cybercriminals often use threats that your security has been compromised. So, watch out for fake alerts.
- Watch out for spoofs of a popular website or company. Scam artists use graphics in email that appear to be connected with legitimate websites but actually take you to phone scam sites or legitimate-looking pop-up windows. They also use web addresses that resemble the names of well-known companies but are slightly altered or misspelled.
UF Information Security and Compliance publishes alerts about these attacks routinely on the UF IT Alerts website: https://alerts.it.ufl.edu/. At the time this article was first posted there were 5 alerts related to Phishing Scams listed on this page. Additionally, they have some of their own information about phishing available on their website (https://security.ufl.edu/resources/email-safety/phishing/) and also offer two classes that go into the above tips, and much more, in greater detail. You can find them through myTraining in the UF portal.
| Cyber Security at UF | course UF_ITT100_I in myTraining |
| Cyber Safeguards for Restricted Data | https://training.it.ufl.edu/training/items/cyber-safeguards-for-restricted-data.html |
