UFIT expects to deploy new features to the campus email service on September 26, 2017. The new features, known as ProofPoint Targeted Attack Protection (TAP), are an expansion of UF’s existing SPAM and PHISHING protection provided by its ProofPoint system.
On Tuesday, Sept 26th UFIT will enable TAP for all user mailboxes in the on-premise UF/AHC Exchange system. A later phase will address Student mailboxes and other, more obscure, fringe mail-flow.
When TAP is enabled, any email received by users in the on-premise UF/AHC Exchange system from outside UF’s email system will have the following protective measures taken:

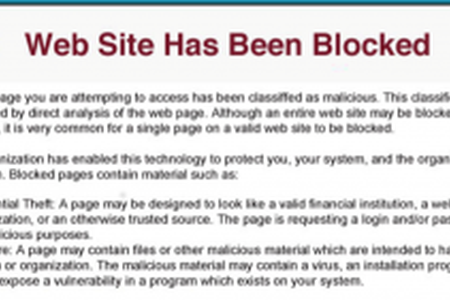
- URL Defense: All URLS (web links) in email will be rewritten to point to a ProofPoint service, within https://urldefense.proofpoint.com, that will block access to harmful URLs. Safe URLs will be automatically passed to the original site. However, if the URL is malicious you will encounter a “Web Site Has Been Blocked!” page.
- Attachment Defense: Certain email attachments, Microsoft Office documents, PDF, RTF, HTML and SWF, will receive additional screening for malware and other harmful behaviors. This includes these file types within archive files (zip, tar, rar, etc). This additional inspection may cause delay delivery of emails from outside the university which contain attachments.
A recent UFIT News article (which has since been removed) introduced this service to UF. UFIT also added more information about it on the UF Email webpage (however, again, the information was removed). Engineering IT Support has also added this information to our homepage.
If you have questions, your local IT should be able to help.
Updated: 2017-09-19
A clarification based on a couple of inquiries to UFIT regarding the behavior of URL rewriting during the initial deployment:
- *.ufl.edu URL’s will not be re-written, even if sent from remote email addresses.
- non-ufl.edu domains/URL’s will be re-written from non-ufl email accounts.
- non-ufl.edu domains/URL’s do NOT get re-written if sent from ufl email accounts TO ufl email accounts.
Once this is successfully deployed to faculty, staff, and student mailboxes UFID will tackle the reconfiguration and re-architecture of mail flow such that internal generated emails within all UFL domains also go through TAP URL re-writing. This is a bit more complicated and requires careful changes in the infrastructure and extensive testing to avoid mail loops.
More to come once UFIT is ready to take the next steps.